In boardrooms and compliance meetings, a single phrase has acquired almost magical powers: "We need data sovereignty."
It emerges in conversations about AI infrastructure, cloud computing, and data management like a trump card that immediately ends debate and justifies major infrastructure decisions.
Data sovereignty refers to the legal, regulatory, and contractual requirements governing where data is stored, processed, and who has authority over it. It is often confused with data residency or self-hosted infrastructure, but these are not the same thing.
The phrase carries weight because it invokes both security and regulatory authority simultaneously.
Yet this invocation often masks a profound misunderstanding of what data sovereignty actually entails and whether it truly necessitates self-hosting infrastructure.
The appeal is understandable. In an era of increasing regulatory complexity and high-profile data breaches, maintaining complete control over data feels both prudent and protective. It suggests fortress-like security, unambiguous compliance, and independence from external vendors.
When a CTO proposes a self-hosting solution for an AI infrastructure platform and justifies it through data sovereignty requirements, the argument carries intuitive force. How could anyone argue against your organization maintaining direct control of its most valuable assets?
The problem is that "data sovereignty" has become an umbrella term conflating multiple distinct concepts, each with different technical implications and compliance consequences.
When executives cite data sovereignty as justification for self-hosting, they're often simultaneously referring to data residency requirements, regulatory compliance obligations, contractual commitments, and internal governance policies. These are not synonymous.
An organization might have stringent data residency requirements but face less demanding compliance obligations than a cloud provider already manages. Another might need complete IP protection but have no actual regulatory constraints on data location. A third might be pursuing data sovereignty for operational control, not compliance.
This conflation matters enormously because each distinct meaning of "data sovereignty" points toward different solutions. Some genuinely require self-hosting.
Others can be satisfied through cloud infrastructure with specific contractual terms. Still others are best addressed through hybrid architectures or managed platforms that provide contractual data control without requiring an organization to become its own infrastructure operator.
By treating data sovereignty as a monolithic concept pointing inevitably toward self-hosting, organizations risk making expensive infrastructure decisions that create far more problems than they solve.
What Data Sovereignty Requires (Beyond Self-Hosting)
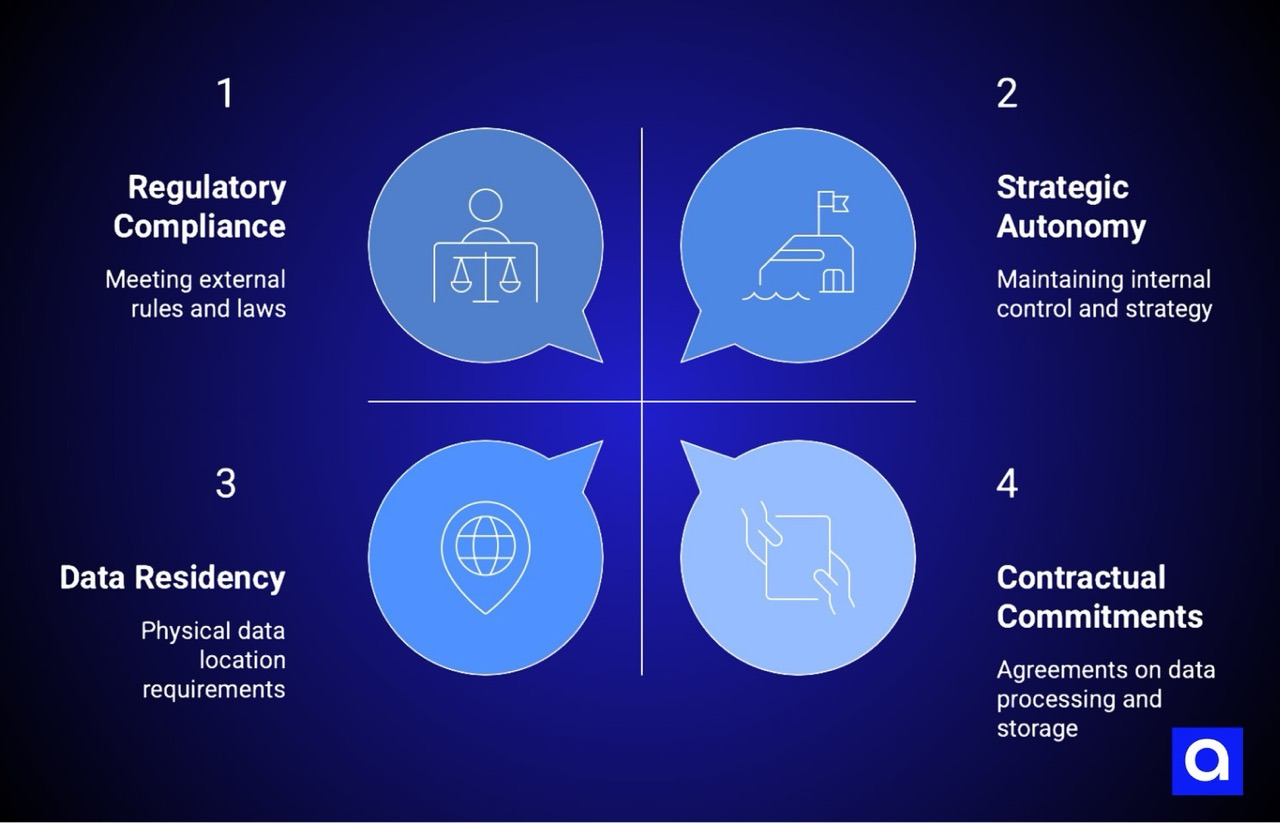
Data sovereignty describes several distinct technical and legal states, and clarity about which one an organization actually requires is essential to sound infrastructure decisions.
The first and most commonly cited meaning concerns data residency: the requirement that data remain physically located within specific geographic boundaries. Data residency requirements typically emerge from regulatory frameworks. The European Union's GDPR requires that personal data be processed in accordance with specific rules and, in certain contexts, demands that data remain within EU borders.
China's regulations impose stringent data residency requirements on any data generated within Chinese territory. India has been moving toward more rigorous data localization requirements. Australia, Canada, and many other jurisdictions have implemented specific data residency requirements for particular data categories, especially health information and government-related data.
Data residency requirements are fundamentally about where data physically resides at rest and potentially where processing occurs. These requirements can often be satisfied through cloud providers that operate regional data centers in the jurisdictions where residency is required. A company subject to GDPR can use AWS Ireland or Google Cloud Europe without implementing any self-hosted infrastructure. The cloud provider maintains the data within EU boundaries, maintains appropriate security and governance controls, and demonstrates compliance through regular audits and certifications. The organization maintains its own data governance and contractual relationships but relies on the provider's infrastructure. This satisfies data residency requirements without requiring self-hosting.
The second meaning of data sovereignty concerns industry-specific regulatory compliance beyond data residency.
HIPAA in healthcare, for instance, does not technically mandate data residency but does require that organizations ensure appropriate safeguards, encryption, access controls, and audit capabilities. HIPAA can theoretically be satisfied by cloud providers who meet the security requirements and sign Business Associate Agreements, though we've observed that some healthcare organizations elect to self-host believing it provides clearer compliance evidence.
Financial services regulations similarly focus on security controls, audit trails, and compliance demonstration rather than on data location per se. Many financial institutions use cloud platforms while maintaining compliance through careful architecture and contractual terms.
The third dimension of data sovereignty involves contractual obligations and commercial commitments. Organizations might have specific data-sharing agreements with customers, partners, or clients that specify where data is processed and stored.
An AI infrastructure platform might commit to customers that data will not be processed by third parties or will only be processed within specific geographic regions. These contractual requirements do genuinely constrain infrastructure choices, but they do not necessarily require self-hosting.
A managed platform operated by the infrastructure provider in specific regions can satisfy contractual commitments just as effectively as self-hosted infrastructure, provided the contractual terms clearly establish where data is processed and who has access to it.
The fourth and often overlooked dimension of data sovereignty concerns internal governance policies, organizational risk tolerance, and strategic decisions that have little to do with external compliance.
Some organizations decide that their intellectual property is sufficiently valuable and distinctive that they should not rely on cloud infrastructure providers' security practices.
Others make this determination based on the sensitive nature of their business operations. Still others have experienced data breaches or security incidents that create organizational preferences for self-hosting.
These are legitimate organizational concerns, but they represent internal policy choices rather than compliance requirements. Conflating them with actual regulatory mandates creates confusion about what is required versus what is preferred.
A realistic assessment of data sovereignty requirements thus demands clear answers to specific questions.
First, are there actual regulatory mandates on data residency that constrain where data can physically be stored?
Second, do industry-specific compliance frameworks require specific security controls, access patterns, or audit capabilities that cannot be achieved through managed providers?
Third, do contractual commitments to customers or partners specify data locations or processing constraints? Fourth, what internal policies and governance frameworks has the organzation established for data management?
Each of these questions typically points toward different solutions, and treating them as interchangeable aspects of a single "data sovereignty" requirement leads to infrastructure decisions that are misaligned with actual business needs.
How Sovereign Cloud & Managed Platforms Achieve Compliance
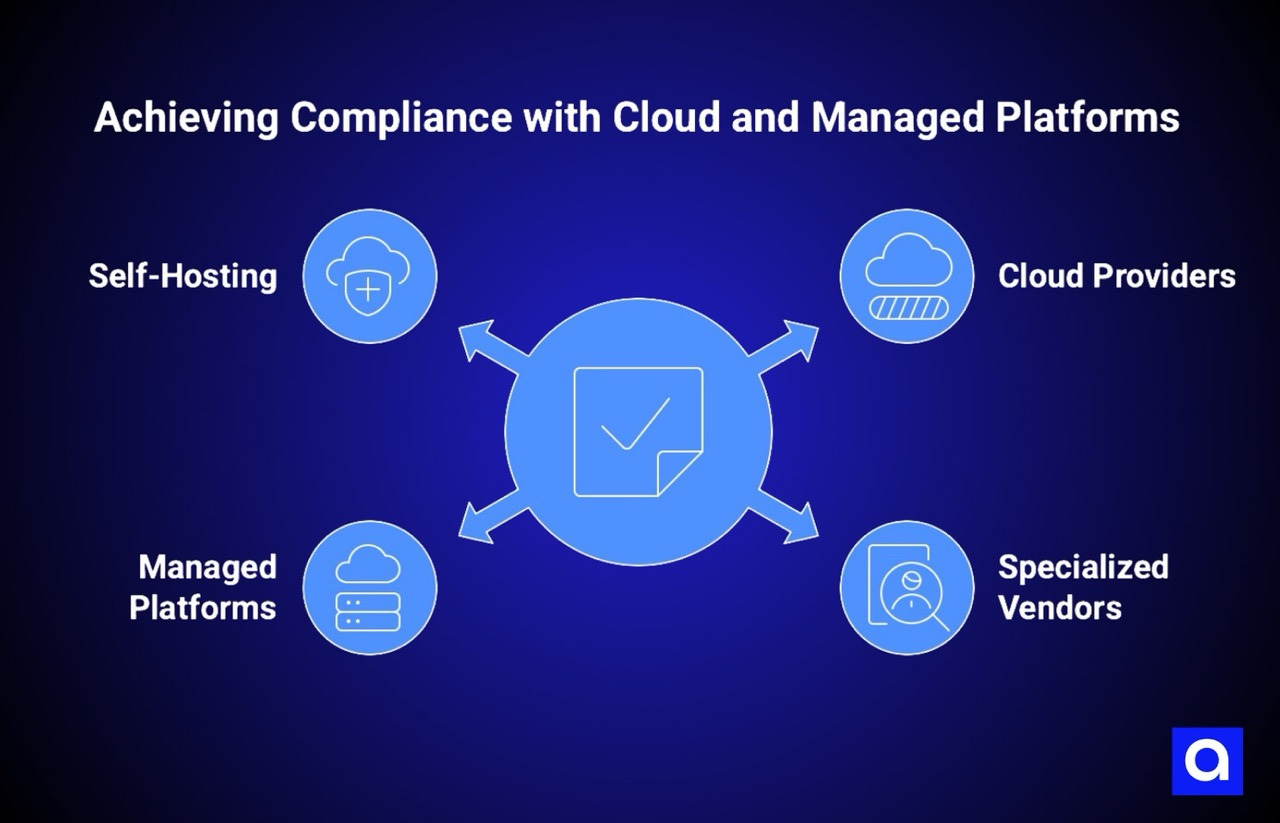
The fundamental error in many organizations' infrastructure decision-making is the leap from identifying a compliance requirement to assuming that self-hosting is the only way to meet it.
This leap reflects both a misunderstanding of cloud provider capabilities and an underestimation of the compliance risks inherent in self-hosted infrastructure. In our work with clients, we've found that sophisticated cloud providers and managed infrastructure platforms satisfy most data sovereignty requirements more effectively than self-hosted solutions.
Consider first the regulatory compliance landscape around data residency. Cloud providers like Amazon Web Services, Microsoft Azure, and Google Cloud have invested heavily in regional infrastructure specifically to support customers with data residency requirements.
AWS operates in 33 geographic regions, each containing multiple availability zones with redundant infrastructure. Each region is completely separate from others, allowing customers to specify that data should never leave a particular region. The infrastructure is regularly audited by independent third parties, and these providers maintain extensive documentation proving compliance with GDPR, HIPAA, FedRAMP, and dozens of other regulatory frameworks.
For an organization in the EU subject to GDPR, using AWS Europe provides robust compliance demonstration through the provider's certifications and audit reports. A self-hosted solution in the same geographic location would need to implement equivalent security, achieve equivalent compliance certifications, and maintain equivalent audit documentation. The regulatory compliance benefit of self-hosting in this context is illusory because the compliance requirement is satisfied equally by either approach.
API providers and specialized infrastructure vendors offer similar capabilities for specific workloads and compliance contexts. These providers operate in regulated industries and have built their businesses around meeting strict compliance requirements.
We've observed that healthcare AI platforms, financial services infrastructure providers, and other specialized vendors maintain regional deployments and comprehensive compliance documentation. They have smaller surface areas than hyperscale cloud providers, which can actually reduce complexity in certain contexts.
An organization deploying sensitive AI models for healthcare applications might find a specialized healthcare AI provider more suitable than general-purpose cloud infrastructure, not because of data sovereignty per se but because the provider has purpose-built compliance frameworks, security practices tuned to healthcare risks, and contractual terms aligned with healthcare industry norms.
Managed platforms like Valkyrie represent an emerging category of solutions that sit between hyperscale cloud providers and fully self-hosted infrastructure, offering particularly nuanced options for organizations with data sovereignty concerns.
These platforms provide regional deployment options that ensure data remains within specified geographic boundaries, HIPAA and GDPR compliance support through carefully architected systems and audit frameworks, and contractual commitments that bind the platform operator to data residency and security requirements.
Unlike self-hosted infrastructure that requires the organization to become its own operator, and unlike general-purpose cloud platforms that might seem distant from specific compliance needs, managed platforms are specifically designed to balance data control requirements with operational sophistication.
The critical insight is that cloud providers and managed platforms achieve compliance through three complementary mechanisms.
First, they offer technical controls that enforce data residency and security requirements at the infrastructure level. Data is encrypted at rest and in transit, access logs are maintained, and regional boundaries are technically enforced.
Second, they undergo regular independent audits by compliance specialists who verify that systems meet regulatory requirements. These audit reports, certifications, and attestations provide the compliance evidence that regulators and compliance officers need.
Third, they maintain contractual commitments to customers that specify data handling practices and back those commitments with explicit liability provisions. A cloud provider that violates a Data Processing Agreement faces contractual liability, giving the provider strong incentives to maintain compliance.
Self-hosted infrastructure must achieve the same three mechanisms independently. The organization must implement equivalent technical controls, must achieve equivalent compliance certifications through independent audits, and must maintain its own liability frameworks.
The difference is that a self-hosted approach places all of these burdens on the organization rather than distributing them across a provider that operates infrastructure for many customers.
A healthcare organization that self-hosts AI infrastructure must implement HIPAA compliance controls, must undergo annual HIPAA audits, must maintain Business Associate Agreements with any subcontractors, and must manage the liability implications if something goes wrong.
A healthcare organization that uses a managed healthcare AI platform with HIPAA certification has shifted these burdens to the provider while maintaining contractual oversight. The compliance outcome is equivalent, but the operational burden is substantially different.
As a result, organizations increasingly treat cloud and DevOps capabilities as compliance enablers rather than risk factors.
What’s The True Cost of Self-Hosting for Compliance?
Organizations considering self-hosting as a solution to data sovereignty requirements typically focus on hardware costs, software licensing, and facility expenses. These are real and measurable costs, but they represent only a fraction of what it actually costs to achieve compliance through self-hosting.
A more honest accounting requires considering certification and audit costs, ongoing security investment, operational expertise requirements, documentation burden, and risk exposure. When we've evaluated these costs for clients, self-hosting often appears far more expensive than cloud or managed platform alternatives.
Compliance certification and auditing expenses are among the most underestimated costs in self-hosting decisions. Achieving HIPAA certification requires a thorough security assessment by qualified auditors, remediating any identified vulnerabilities, documenting all controls, and then maintaining compliance through regular audits.
The initial assessment and remediation typically cost between $50,000 and $200,000 for an organization of modest size, with costs scaling upward for larger deployments. Annual recertification audits typically cost $15,000 to $50,000 per year depending on the organization's size and complexity.
SOC 2 Type II certification, often required by customers and partners, demands ongoing audit engagement and typically costs $20,000 to $50,000 annually. FedRAMP certification, if required for government contracting, can cost $1 million or more. GDPR compliance auditing costs similarly, particularly when the organization must demonstrate compliance across multiple regions and data processing activities.
These certification costs reflect real work: security experts must examine systems, verify that controls are implemented correctly, test that security mechanisms function as intended, and document everything for regulatory review. This work cannot be skipped if compliance is genuinely required.
But many cloud providers and managed platforms have already invested in these certifications and maintain ongoing compliance.
AWS maintains current FedRAMP, HIPAA, SOC 2, and GDPR compliance certifications across all regions. Microsoft Azure similarly maintains comprehensive compliance credentials.
Specialized managed platforms like Valkyrie are built with specific compliance frameworks as core architectural decisions. By using a certified provider or platform, an organization eliminates most of the cost of achieving compliance certifications directly. The organization still needs to verify that the provider's certifications are appropriate for its use case and maintain its own compliance documentation of how the platform is used, but the fundamental certification burden is borne by the provider.
Security investment represents a second major cost category that self-hosting requires but is rarely visible in initial infrastructure budgets. Compliance frameworks specify security controls that must be implemented and maintained.
HIPAA requires encrypted data at rest and in transit, access controls, audit logging, vulnerability management, and incident response capabilities. GDPR requires similar controls plus explicit data protection impact assessments.
These controls must be implemented across infrastructure, applications, and operational processes. Implementing encryption across a self-hosted deployment requires choosing encryption algorithms, generating and managing encryption keys, implementing encryption in applications and storage systems, and establishing processes for key rotation and recovery.
Each of these steps involves security expertise that many organizations do not have in-house. Implementing comprehensive access controls requires directory services, privileged access management, role-based access controls, and multifactor authentication.
Maintaining audit logging requires collecting logs from infrastructure components, securely storing them, and maintaining systems that prevent log tampering. These are non-trivial security engineering challenges.
The alternative approach, using a managed platform that has already implemented these controls, transfers this engineering burden to the platform operator. The organization still needs to configure access controls for its specific use cases and verify that the platform's security capabilities meet its requirements, but the platform operator has already invested in implementing, testing, and auditing security controls.
This investment is spread across the platform operator's customer base, making it far more cost-effective than each customer implementing equivalent controls independently. For an organization that is not itself a security infrastructure specialist, this transfer of burden typically results in better security outcomes at lower cost than self-hosting.
Operational expertise represents a third major cost. Running production infrastructure requires people who understand infrastructure operations, can respond to incidents, maintain systems, and troubleshoot problems when things go wrong.
An organization that self-hosts must employ or contract with people who can manage infrastructure, monitor systems for problems, apply security patches, manage capacity, and respond to incidents. These roles are not part-time: maintaining production infrastructure requires dedicated personnel.
An organization with modest infrastructure might require two to three full-time operations professionals, which represents $200,000 to $350,000 in annual compensation plus benefits. As infrastructure grows, these costs scale.
An organization using cloud or managed platform infrastructure still needs operations professionals, but the platform provider's operations team handles much of the routine maintenance, scaling, and incident response. The organization's operations team focuses on managing its specific applications and use cases rather than managing underlying infrastructure.
Documentation burden represents a fourth cost category specific to regulated environments. Compliance frameworks require detailed documentation of systems, controls, and security practices.
HIPAA compliance requires a security plan, risk analysis, policy documentation, employee training records, and documentation of all security incidents and remediations. GDPR requires data protection impact assessments, records of processing activities, privacy policies, and documentation of data retention schedules.
Maintaining this documentation is labor-intensive and must be kept current as systems and practices evolve. Auditors will review this documentation and expect it to accurately reflect actual practice. Creating and maintaining comprehensive compliance documentation for self-hosted infrastructure is typically a part-time role for at least one experienced compliance professional. Using a cloud provider or managed platform that maintains this documentation reduces this burden.
The organization still needs to document its specific use cases and how it leverages the provider's infrastructure, but the fundamental compliance documentation is provided by the provider.
Risk exposure represents the most significant but least quantifiable cost of self-hosting in regulated environments. If a self-hosted system experiences a security incident or compliance violation, the organization bears direct liability. There is no vendor to share responsibility, no contractual recourse, and no insurance to distribute the risk.
A HIPAA violation resulting in unauthorized disclosure of patient data can result in fines of $100 to $50,000 per patient per violation, up to $1.5 million per year per violation category. GDPR violations can result in fines of 4 percent of global revenue or 20 million euros, whichever is greater.
We've observed that healthcare organizations and technology companies experience data breaches regularly, and regulatory fines in the millions of dollars are increasingly common. When an organization uses a managed platform or cloud provider and that provider experiences a compliance violation, the liability is typically shared through contractual agreements. The provider's insurance often covers some portion of the financial risk. While no arrangement can eliminate the risk of a vendor experiencing a security incident, the contractual and financial risk distribution with managed platforms is substantially better than the concentrated risk of self-hosted infrastructure.
When Does Data Sovereignty May Require Self-Hosting?
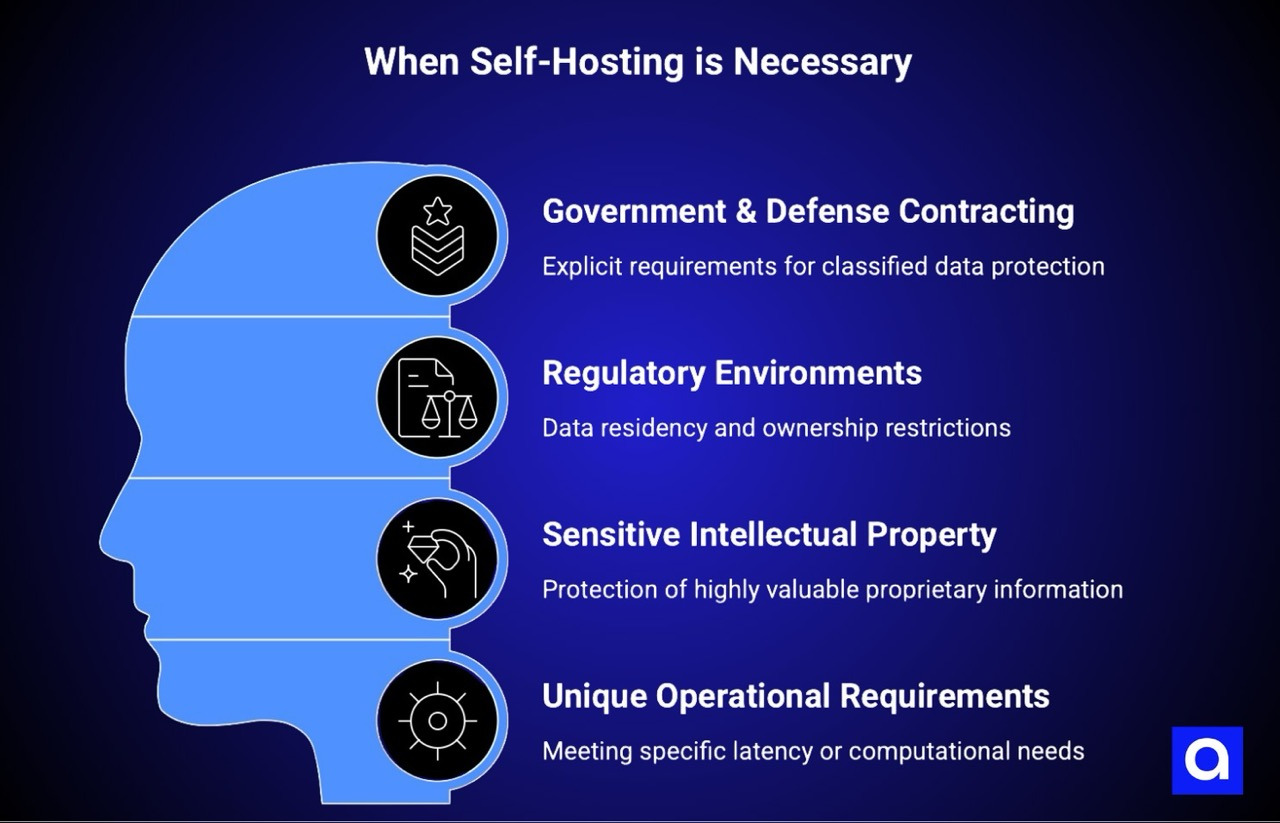
Despite the substantial costs and complexities of self-hosting, there are genuine situations where data sovereignty requirements do necessitate self-hosted infrastructure. These situations are important to identify clearly because they represent the cases where self-hosting is the right choice.
Understanding these cases also illuminates why they are exceptions rather than the rule, which helps organizations avoid extending self-hosting decisions beyond their actual scope.
Government and defense contracting represents the most unambiguous case where self-hosting is required. The U.S. Department of Defense maintains specific requirements for how classified and sensitive unclassified information must be protected, and these requirements are increasingly extending to contractor networks.
Some DoD contracts explicitly prohibit the use of commercial cloud providers and require contractors to maintain dedicated, isolated infrastructure. Similar requirements exist in other countries' defense establishments and in certain intelligence agency contracting.
These requirements reflect a policy decision that certain information must be protected through infrastructure under direct government or contractor control. In these contexts, self-hosting is not one option among many but rather a contractual requirement. An organization contracting with the Department of Defense must implement the required infrastructure or not pursue the contract.
Specific regulatory environments can require self-hosting when data residency requirements are combined with restrictions on foreign ownership or control of infrastructure.
China's regulations, for instance, require that certain types of data be processed within China and prohibit foreign entities from controlling the infrastructure where that processing occurs. This effectively requires organizations operating in China to partner with Chinese entities or establish Chinese subsidiaries to operate infrastructure.
Russia, India, and other countries have implemented similar requirements in specific sectors. These are requirements that combine data location with control.
An international organization operating AI infrastructure in China faces a fundamental constraint: the infrastructure must be controlled by a Chinese entity. This can be achieved through partnerships, joint ventures, or subsidiary operations, but it cannot be achieved through cloud providers that are not organized as Chinese entities. In these jurisdictions, self-hosting becomes not merely an option but a contractual and regulatory necessity.
Extremely sensitive intellectual property represents a third category where self-hosting may be genuinely justified. Some organizations possess proprietary information that is so valuable and so central to competitive advantage that they believe even minimal exposure to external infrastructure providers represents unacceptable risk.
A pharmaceutical company might believe that its drug formulation and development processes are so valuable that these cannot be entrusted to any external infrastructure.
A semiconductor company might feel similarly about its chip design and manufacturing processes.
An AI research laboratory might determine that its most advanced models represent proprietary technology that should not be processed on any infrastructure that is not under complete organizational control.
These decisions reflect reasonable risk assessment by organizations with genuinely exceptional intellectual property.
However, they also represent edge cases. For most AI infrastructure applications, the sensitivity of intellectual property does not justify the costs and operational complexities of self-hosting.
Unique operational requirements can occasionally justify self-hosting when an organization's infrastructure needs diverge substantially from what commercial platforms offer.
An organization with extreme latency requirements that make cloud providers unsuitable, or with highly specialized computational requirements that cannot be accommodated through standard cloud offerings, might find self-hosting necessary.
Similarly, an organization operating in an environment with limited internet connectivity or severe network constraints might find that self-hosted infrastructure is more practical than relying on cloud connectivity.
An organization managing life-critical systems with extraordinarily high availability requirements might determine that self-hosted infrastructure with complete operational control offers advantages over cloud platforms.
These are legitimate operational reasons for self-hosting, though they reflect infrastructure requirements rather than data sovereignty per se. They do demonstrate that self-hosting can be justified on grounds other than compliance, but they also highlight why self-hosting decisions should be based on specific operational requirements rather than on abstract notions of data sovereignty.
Data Classification and Architecture for Data Sovereignty
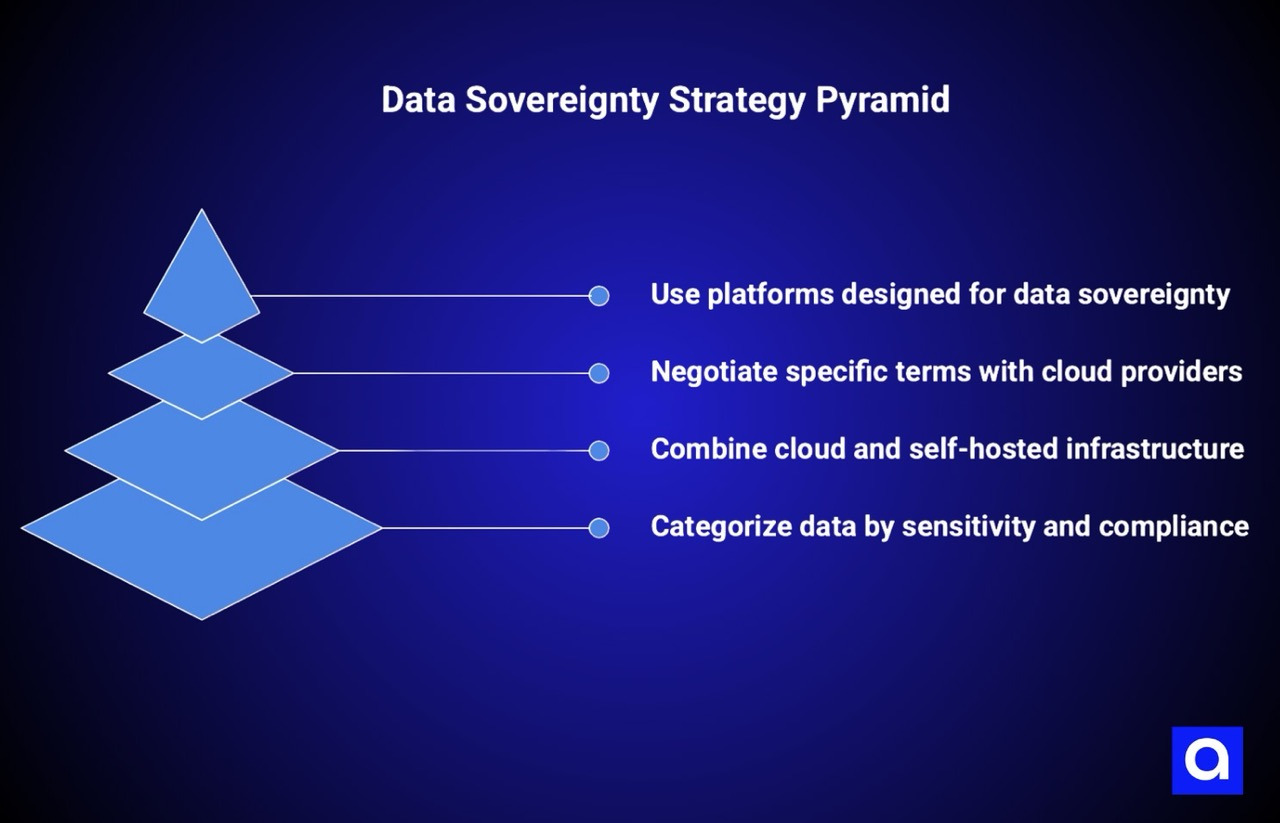
Organizations that believe they need data sovereignty should start with a more nuanced approach than jumping to self-hosting. This approach begins with clear data classification that distinguishes between different types of data and applies appropriate governance to each category.
Not all organizational data has equivalent sensitivity or compliance requirements. Customer personal data subject to GDPR might require specific data residency, while internal operational data might not. Proprietary AI models might require enhanced security, while training datasets might be easier to manage. Sensitive health information subject to HIPAA might require specific access controls, while anonymized research data might require less stringent protection.
By classifying data according to sensitivity and regulatory requirements, organizations can apply sophisticated solutions that match the actual risk and compliance profile of each data category.
This data classification approach enables organizations to leverage cloud provider and managed platform capabilities for the majority of their data while potentially implementing specialized controls or isolated infrastructure for data that genuinely requires it.
An organization might store most of its data in a compliant cloud environment while maintaining a smaller self-hosted infrastructure for its most sensitive proprietary algorithms or highest-risk datasets.
This hybrid approach often provides better protection for genuinely sensitive information while avoiding the operational burden of self-hosting everything. The organization gains the benefits of cloud infrastructure—scalability, managed operations, built-in compliance—for the bulk of its workload while maintaining direct control over its highest-risk assets.
Leveraging provider compliance certifications and contractual commitments represents another approach that often eliminates the need for self-hosting while still ensuring data sovereignty. Rather than treating cloud providers as generic commodity infrastructure, organizations can negotiate specific contractual terms and verify that providers maintain specific compliance certifications.
A healthcare organization can ensure that its cloud provider maintains HIPAA certification and sign a Business Associate Agreement that specifies exactly how data will be protected.
A European organization can ensure that its provider maintains GDPR compliance and specify in contracts that data will not be transferred outside the EU.
An organization concerned about data sovereignty can include contractual provisions that limit how data is accessed internally, restrict where it can be processed, and establish clear procedures for data deletion.
These contractual approaches provide many of the control benefits of self-hosting while avoiding the operational burden.
Hybrid architectures that combine managed infrastructure with specific control points can address data sovereignty concerns while maintaining operational manageability.
An organization might use a managed AI infrastructure platform like Valkyrie for model hosting and serving, which provides HIPAA and GDPR compliance support and regional deployment options, while maintaining direct control over sensitive data ingestion and transformation processes through dedicated infrastructure.
The organization might implement encryption and key management systems that it operates directly, ensuring it maintains exclusive control over encryption keys. It might establish dedicated data validation and governance pipelines that run on its own infrastructure before data is transferred to the managed platform.
This approach provides clear data control and sovereignty over the most sensitive operational aspects while leveraging managed platform capabilities for the technically complex infrastructure components that do not inherently require self-hosting.
Managed platforms designed with data sovereignty in mind offer another option that sits between self-hosted infrastructure and general-purpose cloud platforms. These platforms are specifically architected to provide regional deployment, compliance support, and data control capabilities.
Platforms that support HIPAA, GDPR, and other compliance frameworks from the ground up can often provide compliance evidence more efficiently than self-hosted infrastructure because compliance is built into the platform architecture rather than added on top of generic infrastructure.
Regional deployment options ensure that data remains within specified geographic boundaries. Contractual commitments bind the platform operator to data handling practices and data residency requirements.
This approach enables organizations to achieve data sovereignty objectives without bearing the full operational burden of self-hosting while also benefiting from infrastructure specifically designed for compliance-sensitive workloads.
Building the Business Case for Self-Hosting vs Cloud Infrastructure
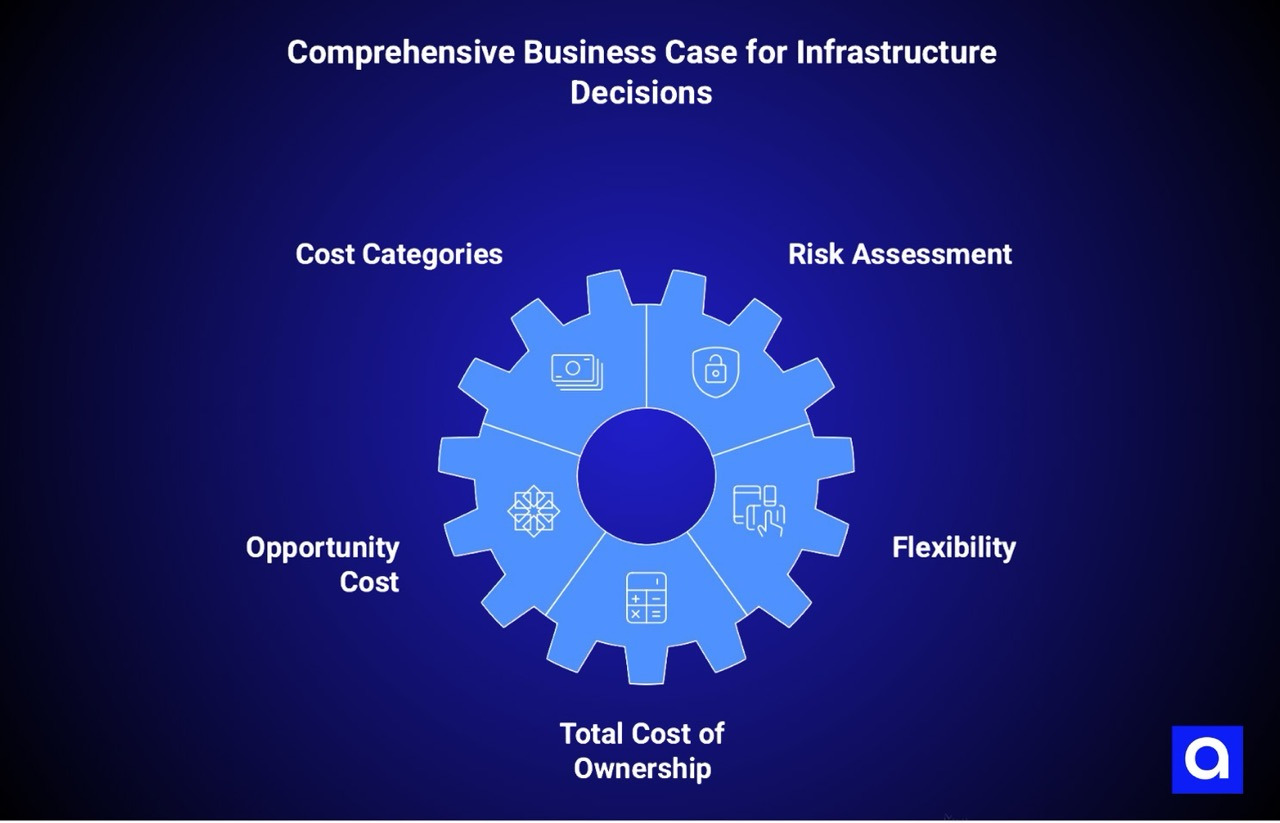
A rigorous decision about self-hosting versus cloud versus managed platforms requires a complete business case that includes all relevant cost categories and explicitly accounts for risk.
This business case should begin by establishing clear cost categories: hardware and facility costs for self-hosted infrastructure, cloud platform subscription fees for cloud alternatives, or managed platform fees. These are the obvious costs, but they represent only part of the true cost of ownership.
The business case should then enumerate less obvious costs that self-hosting requires. Initial compliance certification and audit costs should be estimated based on the specific regulatory requirements the organization faces.
Annual recertification costs should be included as ongoing expenses for the lifetime of the infrastructure. Security engineering costs for implementing and maintaining security controls should be estimated either as the cost of hiring security personnel or as contractor fees if the organization outsources this function. Operational staffing costs for running the infrastructure should be included, including salary and benefits for infrastructure engineers, operations professionals, and security personnel.
Documentation and compliance management costs, including the time of compliance professionals, should be estimated. Software licensing costs for security, monitoring, and compliance tools should be included. Finally, costs associated with incident response, security updates, and ongoing maintenance should be estimated based on industry experience.
The business case should explicitly include risk assessment and compare the risk exposure of different approaches. This comparison should include the probability of different types of security incidents occurring, the estimated financial impact of those incidents, and the way risk is distributed across the organization and any external vendors.
A self-hosted approach concentrates risk entirely on the organization. A cloud or managed platform approach distributes risk through contractual agreements and insurance mechanisms. While no approach completely eliminates risk, the financial implications of different risk profiles should be explicitly modeled.
The business case should also account for opportunity cost and flexibility. Implementing and operating self-hosted infrastructure consumes engineering time and operational attention that could be directed toward building and improving the organization's core applications and business logic.
An organization that dedicates five engineers to infrastructure operations is not dedicating those engineers to developing AI models, implementing features, or improving its core products. Cloud and managed platform approaches reduce this opportunity cost by transferring infrastructure responsibilities to external entities.
Similarly, infrastructure flexibility differs substantially between approaches. An organization that needs to scale infrastructure rapidly or experiment with new approaches might find cloud platforms more flexible than self-hosted infrastructure that requires capacity planning and hardware procurement cycles.
The complete business case should compare total cost of ownership across a multi-year timeframe for each approach. It should include capex costs upfront for self-hosted infrastructure, the ongoing opex costs of operating it, the personnel costs required, the compliance and certification costs, risk-adjusted financial impacts of potential incidents, and opportunity costs. It should compare this total cost against the cost of using cloud platforms or managed platforms over the same timeframe, including subscription fees, any required architectural modifications, and reduced personnel requirements.
Most organizations conducting this rigorous analysis find that cloud and managed platforms are significantly less expensive than self-hosting for workloads that do not have specific requirements that mandate self-hosting.
Moving Beyond Sovereignty Theater: Effective Data Protection vs Perceived Control
We've observed that data sovereignty has become a form of "sovereignty theater"—decisions that feel protective and sound good in compliance meetings but do not actually deliver superior protection.
An organization that self-hosts infrastructure without the benefit of decades of infrastructure engineering expertise, without the benefit of large-scale security operations, and without independent audit verification may actually have worse data protection outcomes than an organization that uses a well-managed cloud or platform provider.
The infrastructure expertise gap is real and often overlooked. Cloud providers like AWS employ thousands of infrastructure engineers who specialize in security, scalability, reliability, and compliance.
These engineers have collectively designed systems that handle billions of transactions daily, that achieve 99.99 percent uptime, that implement sophisticated monitoring and incident response, and that maintain compliance across multiple regulatory frameworks simultaneously.
Few organizations have the infrastructure expertise to match this depth of specialization. An organization with a handful of infrastructure engineers attempting to build and operate equivalent systems is operating at a significant disadvantage. Self-hosting infrastructure without this level of expertise typically results in less robust infrastructure than commercial platforms provide.
Similarly, security operations at scale represent a competency that most organizations do not possess. Large managed platforms maintain 24/7 security operations centers staffed with security professionals who monitor for threats, respond to incidents, apply security patches, and maintain threat intelligence.
They employ security researchers who discover vulnerabilities in systems and fix them proactively. They conduct regular penetration testing and security audits. An organization operating self-hosted infrastructure typically cannot match this level of security sophistication.
Even if the organization has competent security professionals, they likely lack the scale of resources and depth of specialization that a security operations center provides.
The audit and compliance expertise gap is similarly stark. Compliance frameworks like HIPAA, GDPR, and FedRAMP are complex and require specialized expertise to implement correctly.
Cloud providers and managed platforms employ compliance specialists who understand these frameworks deeply, who have implemented compliance systems repeatedly, and who maintain current expertise as regulations evolve.
An organization conducting compliance certification for the first time faces a steep learning curve and a higher risk of implementing controls incorrectly. Over time, organizational expertise improves, but the initial gap is substantial.
The core insight is that self-hosting for data sovereignty reasons often reflects a misunderstanding of where data protection risks actually arise. Most data breaches and compliance violations are not caused by cloud providers secretly accessing customer data. They are caused by misconfigurations, inadequate security practices, insufficient access controls, poor patch management, and insider threats.
All of these risks can be better mitigated by cloud providers and managed platforms that have dedicated expertise, sophisticated tooling, and proven processes. Self-hosting concentrates these risks entirely on the organization, which typically has less expertise and fewer resources to manage them.
The self-hosted infrastructure feels more protective because the organization has direct control, but this sense of control often masks inferior security practices and inadequate risk management.
The path forward for organizations with data sovereignty concerns is to move beyond sovereignty theater toward infrastructure decisions grounded in specific business requirements and realistic risk assessment.
This means clearly identifying which compliance requirements actually drive infrastructure decisions and which are subjective preferences or organizational comfort. It means recognizing that compliance requirements can often be satisfied through cloud platforms and managed solutions that offer proven compliance credentials. It means evaluating self-hosting only in cases where specific business requirements genuinely justify the operational complexity, cost, and risk.
For most organizations, this analysis will reveal that cloud or managed platforms are superior choices to self-hosting, even for workloads with significant data sovereignty and compliance requirements.
The future of AI infrastructure lies in platforms and providers that understand data sovereignty not as a marketing slogan but as a specific set of requirements to be met through appropriate architecture, compliance certifications, and contractual commitments.
Organizations should demand that their infrastructure providers demonstrate clear compliance credentials, maintain transparent audit reports, and offer contractual terms that align with specific data protection requirements.
Platforms like Valkyrie that provide regional deployment options, maintain HIPAA and GDPR compliance support, and reduce time to production while providing data control represent the practical evolution beyond the false choice between self-hosting and surrender of all data control.
By adopting this more nuanced approach, organizations can achieve genuine data sovereignty and protection while avoiding the enormous costs and operational complexities of self-hosted infrastructure.
Ready to build compliant AI systems without the operational burden of full self-hosting?
Azumo helps organizations design and deploy secure, production-ready AI platforms with regional data residency, HIPAA and GDPR compliance, and full control over sensitive data, without slowing down innovation.
Contact Azumo to discuss how we can help you move from architecture decisions to production with confidence.


.avif)